bpftime
Userspace eBPF runtime for Observability, Network, GPU & General Extensions Framework
Science Score: 67.0%
This score indicates how likely this project is to be science-related based on various indicators:
-
✓CITATION.cff file
Found CITATION.cff file -
✓codemeta.json file
Found codemeta.json file -
✓.zenodo.json file
Found .zenodo.json file -
✓DOI references
Found 2 DOI reference(s) in README -
✓Academic publication links
Links to: zenodo.org -
○Committers with academic emails
-
○Institutional organization owner
-
○JOSS paper metadata
-
○Scientific vocabulary similarity
Low similarity (12.9%) to scientific vocabulary
Keywords
Keywords from Contributors
Repository
Userspace eBPF runtime for Observability, Network, GPU & General Extensions Framework
Basic Info
- Host: GitHub
- Owner: eunomia-bpf
- License: mit
- Language: C++
- Default Branch: master
- Homepage: https://eunomia.dev/bpftime/
- Size: 19.1 MB
Statistics
- Stars: 1,080
- Watchers: 19
- Forks: 109
- Open Issues: 98
- Releases: 4
Topics
Metadata Files
README.md
bpftime: Userspace eBPF runtime for Observability, Network, GPU & General extensions Framework
bpftime is a High-Performance userspace eBPF runtime and General Extension Framework designed for userspace. It enables faster Uprobe, USDT, Syscall hooks, XDP, and more event sources by bypassing the kernel and utilizing an optimized compiler like LLVM.
📦 Key Features \ 🔨 Quick Start \ 🔌 Examples & Use Cases \ ⌨️ Linux Plumbers 23 talk \ 📖 Slides \ 📚 OSDI '25 Paper
Checkout our documents in eunomia.dev!
bpftime is not userspace eBPF VM, it's a userspace runtime framework includes everything to run eBPF in userspace: loader, verifier, helpers, maps, ufunc and multiple events such as Observability, Network, Policy or Access Control. It has multiple VM backend options support. For eBPF VM only, please see llvmbpf.
⚠️ Note:
bpftimeis currently under active development and refactoring towards v2. It may contain bugs or unstable API. Please use it with caution. For more details, check our roadmap. We'd love to hear your feedback and suggestions! Feel free to open an issue or Contact us.
Why bpftime? What's the design Goal?
- Performance Gains: Achieve better performance by
bypassing the kernel(e.g., viaUserspace DBIorNetwork Drivers), with more configurable, optimized and more arch supported JIT/AOT options likeLLVM, while maintaining compatibility with Linux kernel eBPF. - Cross-Platform Compatibility: Enables
eBPF functionality and large ecosystemwhere kernel eBPF is unavailable, such as on older or alternative operating systems, or where kernel-level permissions are restricted, without changing your tool. - Flexible and General Extension Language & Runtime for Innovation: eBPF is designed for innovation, evolving into a General Extension Language & Runtime in production that supports very diverse use cases.
bpftime's modular design allows easy integration as a library for adding new events and program types without touching kernel. Wishing it could enable rapid prototyping and exploration of new features!
Key Features
- Dynamic Binary rewriting: Run eBPF programs in userspace, attaching them to
UprobesandSyscall tracepoints: No manual instrumentation or restart required!. It cantraceorchangethe execution of a function,hookorfilterall syscalls of a process safely, and efficiently with an eBPF userspace runtime. Can inject eBPF runtime into any running process without the need for a restart or manual recompilation. - Performance: Experience up to a
10xspeedup in Uprobe overhead compared to kernel uprobe and uretprobe. Read/Write userspace memory is also faster than kernel eBPF. - Interprocess eBPF Maps: Implement userspace
eBPF mapsin shared userspace memory for summary aggregation or control plane communication. - Compatibility: use
existing eBPF toolchainslike clang, libbpf and bpftrace to develop userspace eBPF application without any modifications. Supporting CO-RE via BTF, and offering userspaceufuncaccess. - Multi JIT Support: Support llvmbpf, a high-speed
JIT/AOTcompiler powered by LLVM, or usingubpf JITand INTERPRETER. The vm can be built asa standalone librarylike ubpf. - Run with kernel eBPF: Can load userspace eBPF from kernel, and using kernel eBPF maps to cooperate with kernel eBPF programs like kprobes and network filters.
- Integrate with AF_XDP or DPDK: Run your
XDPnetwork applications with better performance in userspace just like in kernel!(experimental)
Components
vm: The eBPF VM and JIT compiler for bpftime, you can choose from bpftime LLVM JIT/AOT compiler and ubpf. The llvm-based vm in bpftime can also be built as a standalone library and integrated into other projects, similar to ubpf.runtime: The userspace runtime for eBPF, including the maps, helpers, ufuncs and other runtime safety features.Attach events: support attaching eBPF programs toUprobes,Syscall tracepoints,XDPand other events with bpf_link, and also the driver event sources.verifier: Support using PREVAIL as userspace verifier, or usingLinux kernel verifierfor better results.Loader: Includes aLD_PRELOADloader library in userspace can work with current eBPF toolchain and library without involving any kernel, Another option is daemon when Linux eBPF is available.
Quick Start: Uprobe
With bpftime, you can build eBPF applications using familiar tools like clang and libbpf, and execute them in userspace. For instance, the malloc eBPF program traces malloc calls using uprobe and aggregates the counts using a hash map.
You can refer to eunomia.dev/bpftime/documents/build-and-test for how to build the project, or using the container images from GitHub packages.
To get started, you can build and run a libbpf based eBPF program starts with bpftime cli:
console
make -C example/malloc # Build the eBPF program example
export PATH=$PATH:~/.bpftime/
bpftime load ./example/malloc/malloc
In another shell, Run the target program with eBPF inside:
console
$ bpftime start ./example/malloc/victim
Hello malloc!
malloc called from pid 250215
continue malloc...
malloc called from pid 250215
You can also dynamically attach the eBPF program with a running process:
console
$ ./example/malloc/victim & echo $! # The pid is 101771
[1] 101771
101771
continue malloc...
continue malloc...
And attach to it:
console
$ sudo bpftime attach 101771 # You may need to run make install in root
Inject: "/root/.bpftime/libbpftime-agent.so"
Successfully injected. ID: 1
You can see the output from original program:
console
$ bpftime load ./example/malloc/malloc
...
12:44:35
pid=247299 malloc calls: 10
pid=247322 malloc calls: 10
Alternatively, you can also run our sample eBPF program directly in the kernel eBPF, to see the similar output. This can be an example of how bpftime can work compatibly with kernel eBPF.
console
$ sudo example/malloc/malloc
15:38:05
pid=30415 malloc calls: 1079
pid=30393 malloc calls: 203
pid=29882 malloc calls: 1076
pid=34809 malloc calls: 8
See eunomia.dev/bpftime/documents/usage for more details.
Examples & Use Cases
For more examples and details, please refer to eunomia.dev/bpftime/documents/examples/ webpage.
Examples including:
- Minimal examples of eBPF programs.
- eBPF
Uprobe/USDTtracing andsyscall tracing:- sslsniff for trace SSL/TLS unencrypted data.
- opensnoop for trace file open syscalls.
- More bcc/libbpf-tools.
- Run with bpftrace commands or scripts.
- error injection: change function behavior with
bpf_override_return. - Use the eBPF LLVM JIT/AOT vm as a standalone library.
- Userspace XDP with DPDK and AF_XDP
- CUDA eBPF Probe/Retprobe Example
In-Depth
How it Works
bpftime supports two modes:
Running in userspace only
Left: original kernel eBPF | Right: bpftime
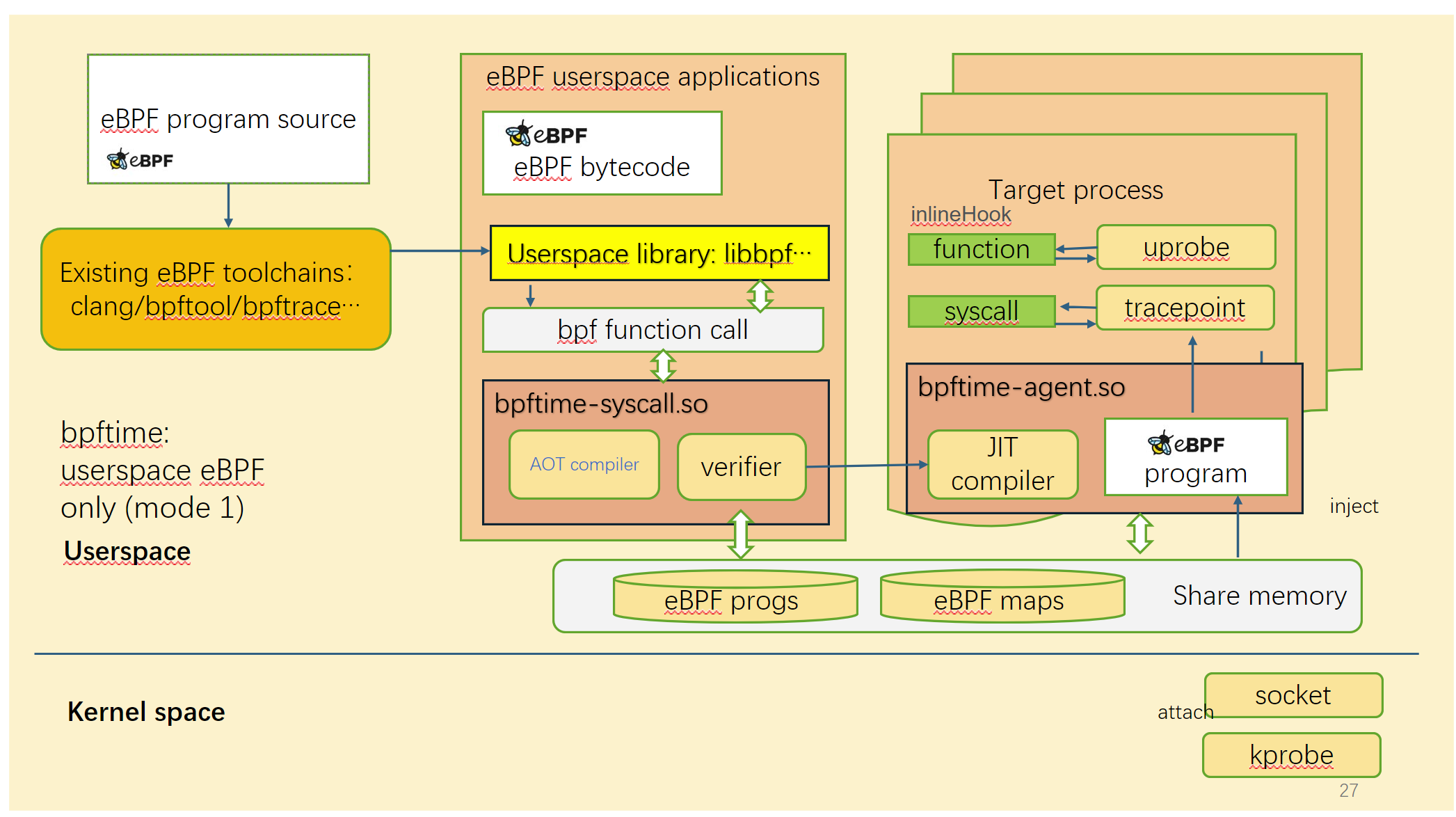
In this mode, bpftime can run eBPF programs in userspace without kernel, so it can be ported into low version of Linux or even other systems, and running without root permissions. It relies on a userspace verifier to ensure the safety of eBPF programs.
Run with kernel eBPF
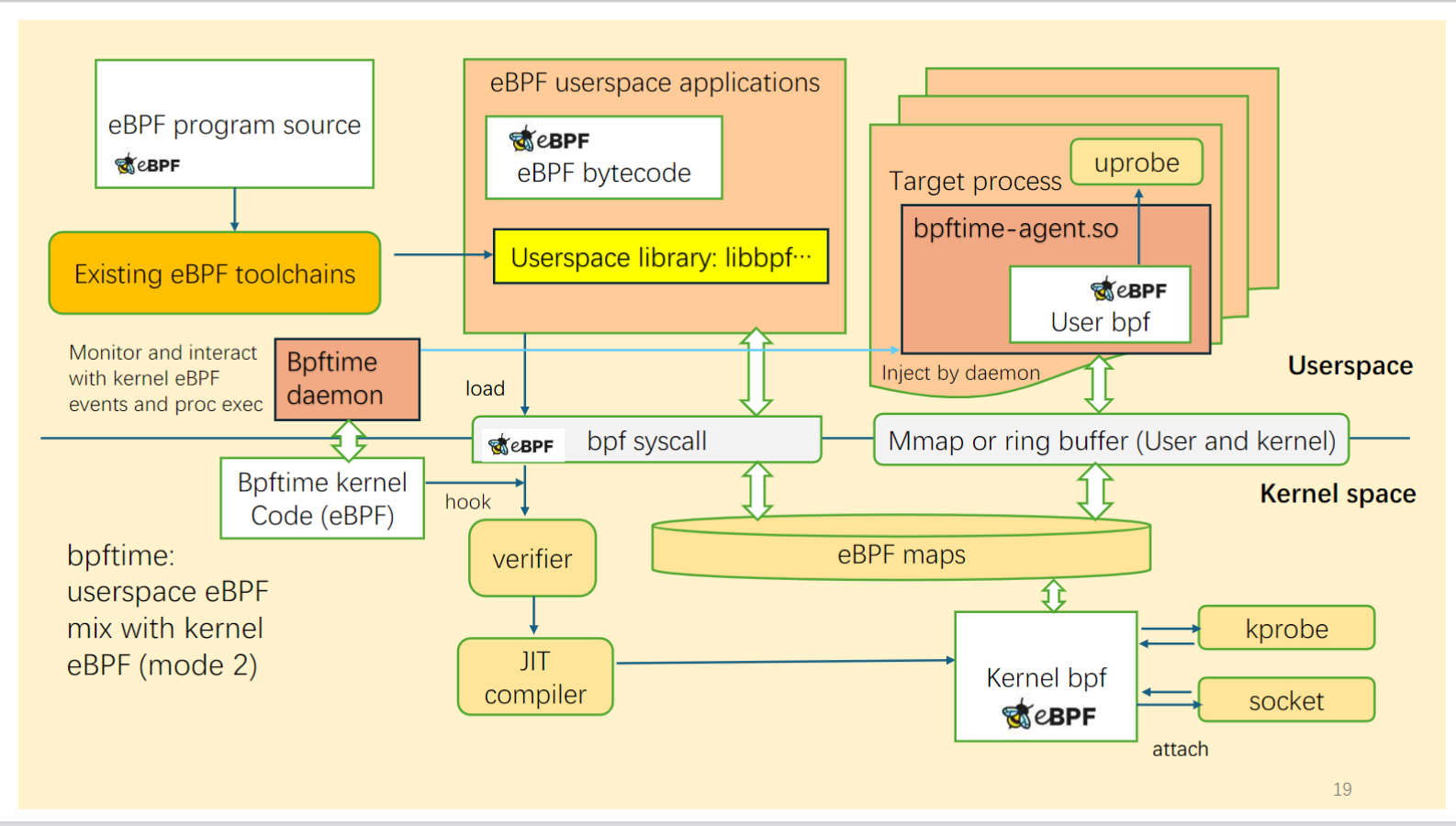
In this mode, bpftime can run together with kernel eBPF. It can load eBPF programs from kernel, and using kernel eBPF maps to cooperate with kernel eBPF programs like kprobes and network filters.
Instrumentation implementation
Current hook implementation is based on binary rewriting and the underly technique is inspired by:
- Userspace function hook: frida-gum
- Syscall hooks: zpoline and pmem/syscall_intercept.
The hook can be easily replaced with other DBI methods or frameworks, or add more hook mechanisms in the future.
See our OSDI '25 paper Extending Applications Safely and Efficiently for details.
Performance Benchmarks
How is the performance of userspace uprobe compared to kernel uprobes?
| Probe/Tracepoint Types | Kernel (ns) | Userspace (ns) | |------------------------|-------------:|---------------:| | Uprobe | 3224.172760 | 314.569110 | | Uretprobe | 3996.799580 | 381.270270 | | Syscall Tracepoint | 151.82801 | 232.57691 | | Manually Instrument | Not avaliable | 110.008430 |
It can be attached to functions in running process just like the kernel uprobe does.
How is the performance of LLVM JIT/AOT compared to other eBPF userspace runtimes, native code or wasm runtimes?

Across all tests, the LLVM JIT for bpftime consistently showcased superior performance. Both demonstrated high efficiency in integer computations (as seen in log2_int), complex mathematical operations (as observed in prime), and memory operations (evident in memcpy and strcmp). While they lead in performance across the board, each runtime exhibits unique strengths and weaknesses. These insights can be invaluable for users when choosing the most appropriate runtime for their specific use-cases.
see github.com/eunomia-bpf/bpf-benchmark for how we evaluate and details.
Hash map or ring buffer compared to kernel(TODO)
See benchmark dir for detail performance benchmarks.
Comparing with Kernel eBPF Runtime
bpftimeallows you to useclangandlibbpfto build eBPF programs, and run them directly in this runtime, just like normal kernel eBPF. We have tested it with a libbpf version in third_party/libbpf. No specify libbpf or clang version needed.- Some kernel helpers and kfuncs may not be available in userspace.
- It does not support direct access to kernel data structures or functions like
task_struct.
Refer to eunomia.dev/bpftime/documents/available-features for more details.
Build and test
See eunomia.dev/bpftime/documents/build-and-test for details.
Roadmap
bpftime is continuously evolving with more features in the pipeline:
- [ ] Keep compatibility with the evolving kernel
- [ ] Refactor for General Extension Framework
- [ ] Trying to refactor, bug fixing for
Production. - [ ] More examples and usecases:
- [X] Userspace Network Driver on userspace eBPF
- [X] Hotpatch userspace application
- [X] Error injection and filter syscall
- [X] Syscall bypassing, batching
- [X] Userspace Storage Driver on userspace eBPF
- [ ] etc...
Stay tuned for more developments from this promising project! You can find bpftime on GitHub.
License
This project is licensed under the MIT License.
Contact and citations
Have any questions or suggestions on future development? Free free to open an issue or contact yunwei356@gmail.com !
Our OSDI '25 paper: https://www.usenix.org/conference/osdi25/presentation/zheng-yusheng
txt
@inproceedings{zheng2025extending,
title={Extending Applications Safely and Efficiently},
author={Zheng, Yusheng and Yu, Tong and Yang, Yiwei and Hu, Yanpeng and Lai, Xiaozheng and Williams, Dan and Quinn, Andi},
booktitle={19th USENIX Symposium on Operating Systems Design and Implementation (OSDI 25)},
pages={557--574},
year={2025}
}
Acknowledgement
eunomia-bpf community is sponsored by PLCT Lab from ISCAS.
Thanks for other sponsors and discussions help building this project: Prof. Marios Kogias from Imperial College London, Prof. Xiaozheng lai from SCUT, Prof lijun chen from XUPT, Prof. Qi Li from THU NISL Lab, and Linux eBPF maintainers in the LPC 23 eBPF track.
Owner
- Name: eunomia-bpf
- Login: eunomia-bpf
- Kind: organization
- Email: team@eunomia.dev
- Location: China
- Website: https://eunomia.dev/
- Repositories: 23
- Profile: https://github.com/eunomia-bpf
Simplify and enhance eBPF programming with Webassembly, and GPT!
Citation (CITATION.cff)
# This CITATION.cff file was generated with cffinit.
# Visit https://bit.ly/cffinit to generate yours today!
cff-version: 1.2.0
title: bpftime
message: >-
If you use this software, please cite it using the
metadata from this file.
type: software
authors:
- given-names: Yusheng
family-names: Zheng
email: yunwei356@gmail.com
affiliation: UC Santa Cruz
- given-names: Tong
family-names: Yu
affiliation: eunomia-bpf Community
- given-names: Yiwei
family-names: Yang
affiliation: UC Santa Cruz
- given-names: Yanpeng
family-names: Hu
affiliation: ShanghaiTech University
- given-names: Xiaozheng
family-names: Lai
affiliation: South China University of Technology
- given-names: Dan
family-names: Williams
affiliation: Virginia Tech
- given-names: Andi
family-names: Quinn
affiliation: UC Santa Cruz
identifiers:
- type: url
value: 'https://www.usenix.org/conference/osdi25/presentation/zheng-yusheng'
description: >-
Extending Applications Safely and Efficiently
repository-code: 'https://github.com/eunomia-bpf/bpftime'
url: 'https://eunomia.dev/bpftime/'
abstract: >-
This paper introduces the Extension Interface Model (EIM) and
bpftime, a framework for safer and more efficient application
extension. EIM treats extension features as resources, allowing
managers to specify exact resource needs. bpftime uses eBPF-style
verification, hardware isolation, and dynamic binary rewriting
to achieve efficiency and compatibility with the existing eBPF
ecosystem. The system demonstrates the approach across 6 use
cases involving security, performance monitoring, and configuration
exploration. By operating in userspace, bpftime achieves significant
performance improvements while maintaining safety guarantees and
compatibility with existing eBPF toolchains.
keywords:
- userspace
- plugin
- eBPF
license: MIT
GitHub Events
Total
- Issues event: 45
- Watch event: 234
- Delete event: 10
- Issue comment event: 124
- Push event: 68
- Pull request review comment event: 99
- Pull request event: 74
- Pull request review event: 96
- Fork event: 27
- Create event: 13
Last Year
- Issues event: 45
- Watch event: 234
- Delete event: 10
- Issue comment event: 124
- Push event: 68
- Pull request review comment event: 99
- Pull request event: 74
- Pull request review event: 96
- Fork event: 27
- Create event: 13
Committers
Last synced: 9 months ago
Top Committers
| Name | Commits | |
|---|---|---|
| Officeyutong | y****x@g****m | 97 |
| 云微 | 1****5@q****m | 93 |
| Nadeshiko Manju | me@m****e | 5 |
| hp | 2****r | 5 |
| Sy03 | 1****0@q****m | 4 |
| Littlefisher619 | i@l****e | 3 |
| NobinPegasus | z****n@g****m | 3 |
| kenlig | 2****g | 3 |
| JiaHuann | c****3@g****m | 2 |
| Shawn Zhong | g****b@s****m | 2 |
| Xu zian | x****1@1****m | 2 |
| dependabot[bot] | 4****] | 2 |
| yuanrui77 | 1****7 | 2 |
| Aneesh Damle | 7****1 | 1 |
| From Scratch | 8****h | 1 |
| Laurențiu Nicola | l****a | 1 |
| NoobZang | r****7@o****m | 1 |
| Nugine | n****e@f****m | 1 |
| Roméo Phang | c****t@p****r | 1 |
| Sanket Teli | 1****0 | 1 |
| VIVEK SATI | v****2@g****m | 1 |
| Zixian Cai | 2****n | 1 |
| fripSide | f****e | 1 |
| Yasir Salaheldin | p****2@g****m | 1 |
Committer Domains (Top 20 + Academic)
Issues and Pull Requests
Last synced: 6 months ago
All Time
- Total issues: 133
- Total pull requests: 162
- Average time to close issues: about 2 months
- Average time to close pull requests: 9 days
- Total issue authors: 37
- Total pull request authors: 23
- Average comments per issue: 2.42
- Average comments per pull request: 1.55
- Merged pull requests: 124
- Bot issues: 0
- Bot pull requests: 3
Past Year
- Issues: 37
- Pull requests: 71
- Average time to close issues: 15 days
- Average time to close pull requests: 12 days
- Issue authors: 22
- Pull request authors: 12
- Average comments per issue: 1.16
- Average comments per pull request: 1.17
- Merged pull requests: 46
- Bot issues: 0
- Bot pull requests: 2
Top Authors
Issue Authors
- yunwei37 (48)
- Officeyutong (39)
- agentzh (27)
- nalreddy (5)
- janetat (4)
- TheAhmad (4)
- hp77-creator (4)
- fr0m-scratch (3)
- liyan-ah (3)
- yidaaichixia (2)
- Sy0307 (2)
- YRXING (2)
- Zheaoli (2)
- NobinPegasus (2)
- JiaHuann (2)
Pull Request Authors
- yunwei37 (87)
- Officeyutong (81)
- Sy0307 (16)
- hp77-creator (12)
- kenlig (6)
- Zheaoli (5)
- NobinPegasus (5)
- yuanrui77 (4)
- yasir-ai (3)
- NoobZang (3)
- zhangzihengya (3)
- ShawnZhong (3)
- aneeshdamle11 (3)
- JiaHuann (3)
- Kailian-Jacy (3)
Top Labels
Issue Labels
Pull Request Labels
Packages
- Total packages: 1
- Total downloads: unknown
- Total dependent packages: 0
- Total dependent repositories: 0
- Total versions: 4
proxy.golang.org: github.com/eunomia-bpf/bpftime
- Homepage: https://github.com/eunomia-bpf/bpftime
- Documentation: https://pkg.go.dev/github.com/eunomia-bpf/bpftime#section-documentation
- License: MIT
-
Latest release: v0.1.0
published 6 months ago
Rankings
Dependencies
- actions/checkout v3 composite
- actions/cache v2 composite
- actions/checkout v2 composite
- actions/setup-python v4 composite
- debian 12 build
- colorama * test
- nose * test
- pyelftools * test
- pytest * test