terrascan
Detect compliance and security violations across Infrastructure as Code to mitigate risk before provisioning cloud native infrastructure.
Science Score: 36.0%
This score indicates how likely this project is to be science-related based on various indicators:
-
○CITATION.cff file
-
✓codemeta.json file
Found codemeta.json file -
✓.zenodo.json file
Found .zenodo.json file -
○DOI references
-
○Academic publication links
-
✓Committers with academic emails
1 of 91 committers (1.1%) from academic institutions -
○Institutional organization owner
-
○JOSS paper metadata
-
○Scientific vocabulary similarity
Low similarity (12.5%) to scientific vocabulary
Keywords
Keywords from Contributors
Repository
Detect compliance and security violations across Infrastructure as Code to mitigate risk before provisioning cloud native infrastructure.
Basic Info
- Host: GitHub
- Owner: tenable
- License: apache-2.0
- Language: Go
- Default Branch: master
- Homepage: https://runterrascan.io
- Size: 15.3 MB
Statistics
- Stars: 5,136
- Watchers: 71
- Forks: 532
- Open Issues: 281
- Releases: 51
Topics
Metadata Files
README.md

Introduction
Terrascan is a static code analyzer for Infrastructure as Code. Terrascan allows you to:
- Seamlessly scan infrastructure as code for misconfigurations.
- Monitor provisioned cloud infrastructure for configuration changes that introduce posture drift, and enables reverting to a secure posture.
- Detect security vulnerabilities and compliance violations.
- Mitigate risks before provisioning cloud native infrastructure.
- Offers flexibility to run locally or integrate with your CI\CD.
Resources
To try Terrascan in your browser, see the Terrascan Sandbox https://www.tenable.com/terrascan
To learn more about Terrascan's features and capabilities, see the documentation portal: https://runterrascan.io
Key features
- 500+ Policies for security best practices
- Scanning of Terraform (HCL2)
- Scanning of AWS CloudFormation Templates (CFT)
- * Scanning of Azure Resource Manager (ARM)
- Scanning of Kubernetes (JSON/YAML), Helm v3, and Kustomize
- Scanning of Dockerfiles
- Support for AWS, Azure, GCP, Kubernetes, Dockerfile, and GitHub
- Integrates with docker image vulnerability scanning for AWS, Azure, GCP, Harbor container registries.
Quick Start
Step 1: Install
Terrascan supports multiple ways to install and is also available as a Docker image. See Terrascan's releases page for the latest version of builds in all supported platforms. Select the correct binary for your platform.
Install as a native executable
sh
curl -L "$(curl -s https://api.github.com/repos/tenable/terrascan/releases/latest | grep -o -E "https://.+?_Linux_x86_64.tar.gz")" > terrascan.tar.gz
tar -xf terrascan.tar.gz terrascan && rm terrascan.tar.gz
sudo install terrascan /usr/local/bin && rm terrascan
terrascan
Install on ArchLinux / Manjaro via AUR
ArchLinux and Manjaro users can install by:
yay -S terrascan
Install via brew
Homebrew users can install by:
sh
$ brew install terrascan
Docker image
Terrascan is also available as a Docker image and can be used as follows
sh
$ docker run tenable/terrascan
Refer to documentation for information.
Step 2: Scan
To scan your code for security issues you can run the following (defaults to scanning Terraform).
sh
$ terrascan scan
Note: Terrascan will exit with an error code if any errors or violations are found during a scan.
List of possible Exit Codes
| Scenario | Exit Code | | ----------- | ----------- | | scan summary has errors and violations | 5 | | scan summary has errors but no violations | 4 | | scan summary has violations but no errors | 3 | | scan summary has no violations or errors | 0 | | scan command errors out due to invalid inputs | 1 |
Step 3: Integrate with CI\CD
Terrascan can be integrated into CI/CD pipelines to enforce security best practices. Please refer to our documentation to integrate with your pipeline.
Terrascan Commands
You can use the terrascan command with the following options:
```sh $ terrascan Terrascan
Usage: terrascan [command]
Available Commands: help Help about any command init Initialize Terrascan scan Detect compliance and security violations across Infrastructure as Code. server Run Terrascan as an API server version Terrascan version
Flags: -c, --config-path string config file path -h, --help help for terrascan -l, --log-level string log level (debug, info, warn, error, panic, fatal) (default "info") -x, --log-type string log output type (console, json) (default "console") -o, --output string output type (human, json, yaml, xml) (default "human")
Use "terrascan [command] --help" for more information about a command. ```
Policies
Terrascan policies are written using the Rego policy language. Every rego includes a JSON "rule" file which defines metadata for the policy. By default, Terrascan downloads policies from Terrascan repositories while scanning for the first time. However, if you want to download the latest policies, you need to run the Initialization process. See Usage for information about the Initialization process.
Note: The scan command will implicitly run the initialization process if there are no policies found.
Docker Image Vulnerabilities
You can use the --find-vuln flag to collect vulnerabilities as reported in its registry as part of Terrascan's output. Currently Terrascan supports Elastic Container Registry (ECR), Azure Container Registry, Google Container Registry, and Google Artifact Registry.
The --find-vuln flag can be used when scanning IaC files as follows:
$ terrascan scan -i <IaC provider> --find-vuln
For more information and explanation of how to setup your environment to authenticate with the registry's APIs see the usage documentation.
Customizing scans
By default, Terrascan scans your entire configuration against all policies. However, Terrascan supports granular configuration of policies and resources.
Read more about in-file instrumentation and the config file on our documentation site.
For now, some quick tips:
- Exclude a particular policy for a specific resource.
- Manually configure policies to be suppressed or applied globally from a scan across all resources or, for just a particular resource.
How to exclude a policy while scanning a resource
You can configure Terrascan to skip a particular policy (rule) while scanning a resource. Follow these steps depending on your platform:
Terraform
Use Terraform scripts to configure Terrascan to skip rules by inserting a comment with the phrase "ts:skip=<RULENAME><SKIP_REASON>". The comment should be included inside the resource as shown in the example below.

Kubernetes
In Kubernetes yamls, you can configure Terrascan to skip policies by adding an annotation as seen in the snippet below.

How to include or exclude specific policies or resources from being scanned
Use the Terrascan config file to manually select the policies which should be included or excluded from the entire scan. This is suitable for edge use cases. Use the "in-file" suppression option to specify resources that should be excluded from being tested against selected policies. This ensures that the policies are skipped only for particular resources, rather than all of the resources.

Sample scan output
Terrascan's default output is a list of violations present in the scanned IaC. A sample output:
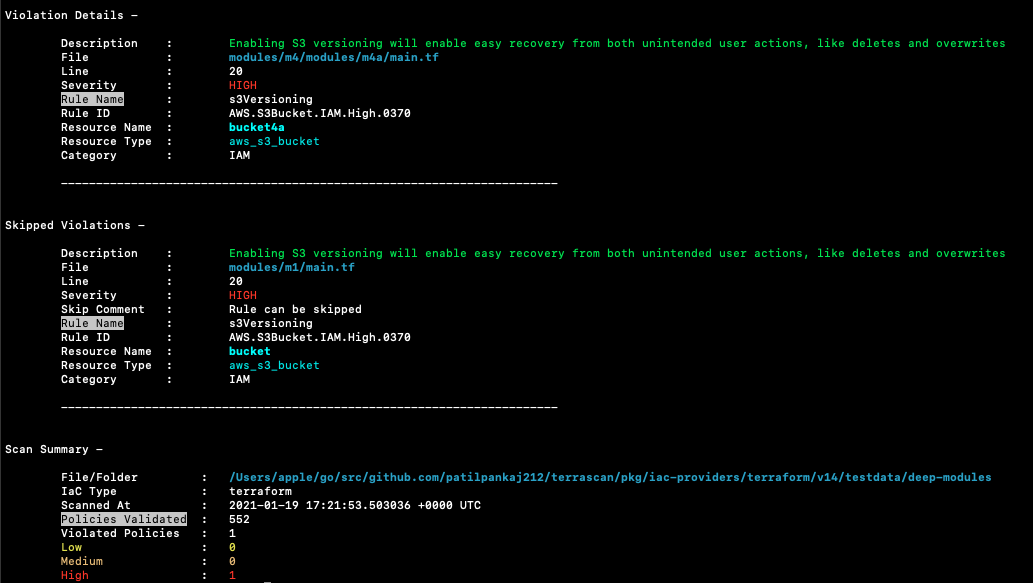
Building Terrascan
Terrascan can be built locally. This is helpful if you want to be on the latest version or when developing Terrascan. gcc and Go 1.19 or above are required.
sh
$ git clone git@github.com:tenable/terrascan.git
$ cd terrascan
$ make build
$ ./bin/terrascan
To build your own docker, refer to this example (Alpine Linux):
``` FROM golang:alpine AS build-env
RUN apk add --update git
RUN git clone https://github.com/tenable/terrascan && cd terrascan \ && CGO_ENABLED=0 GO111MODULE=on go build -o /go/bin/terrascan cmd/terrascan/main.go
```
Developing Terrascan
To learn more about developing and contributing to Terrascan, refer to the contributing guide.
Code of Conduct
We believe having an open and inclusive community benefits all of us. Please note that this project is released with a Contributor Code of Conduct. By participating in this project you agree to abide by its terms.
License
Terrascan is licensed under the Apache 2.0 License.
Stargazers
Forkers
Owner
- Name: Tenable
- Login: tenable
- Kind: organization
- Email: tenable-github@tenable.com
- Location: United States of America
- Website: tenable.com
- Twitter: TenableSecurity
- Repositories: 87
- Profile: https://github.com/tenable
Tenable - the Cyber Exposure company
GitHub Events
Total
- Issues event: 9
- Watch event: 332
- Delete event: 1
- Issue comment event: 68
- Push event: 18
- Pull request review event: 12
- Pull request event: 21
- Fork event: 48
- Create event: 10
Last Year
- Issues event: 9
- Watch event: 332
- Delete event: 1
- Issue comment event: 68
- Push event: 18
- Pull request review event: 12
- Pull request event: 21
- Fork event: 48
- Create event: 10
Committers
Last synced: 9 months ago
Top Committers
| Name | Commits | |
|---|---|---|
| Yusuf Kanchwala | y****f@a****m | 203 |
| Cesar Rodriguez | c****r@a****m | 181 |
| Cesar Rodriguez | t****c@g****m | 169 |
| Pankaj Patil | p****2@g****m | 116 |
| pyup-bot | g****t@p****o | 112 |
| Willie Sana | w****e@a****m | 68 |
| Suvarna Rokade | s****1@g****m | 51 |
| Devang Gaur | d****r@a****m | 49 |
| Gaurav Gogia | 1****a | 45 |
| harkirat22 | h****j@g****m | 38 |
| amirbenv | 7****v | 34 |
| dependabot[bot] | 4****] | 28 |
| Yusuf Kanchwala | 3****f | 24 |
| Nasir Rabbani | 5****i | 21 |
| Jon Jarboe | j****e@g****m | 21 |
| Jon Jarboe | j****n@a****m | 18 |
| nmoretenable | 1****e | 18 |
| Steve Balbach | s****4@s****m | 13 |
| Cesar Rodriguez | c****z@t****m | 12 |
| Shreyas Phansalkar | 7****9 | 12 |
| Jan Hentschel | j****l@u****m | 11 |
| John Kinsella | j****l@g****m | 8 |
| zach.zeid | z****d@g****m | 7 |
| Sangam Biradar | s****4 | 7 |
| Blake Kizer | 6****e | 6 |
| Rui Chen | r****i@m****m | 5 |
| nitumore | n****2@g****m | 5 |
| Kevin Lin | k****n@k****o | 5 |
| Jason Dyke | 1****e | 4 |
| iceal lim | i****l@a****m | 4 |
| and 61 more... | ||
Committer Domains (Top 20 + Academic)
Issues and Pull Requests
Last synced: 6 months ago
All Time
- Total issues: 104
- Total pull requests: 191
- Average time to close issues: 7 months
- Average time to close pull requests: 2 months
- Total issue authors: 93
- Total pull request authors: 31
- Average comments per issue: 2.29
- Average comments per pull request: 2.23
- Merged pull requests: 59
- Bot issues: 0
- Bot pull requests: 74
Past Year
- Issues: 17
- Pull requests: 28
- Average time to close issues: N/A
- Average time to close pull requests: 16 days
- Issue authors: 16
- Pull request authors: 8
- Average comments per issue: 0.82
- Average comments per pull request: 1.21
- Merged pull requests: 14
- Bot issues: 0
- Bot pull requests: 0
Top Authors
Issue Authors
- lisenet (3)
- torbendury (2)
- elchenberg (2)
- balq60 (2)
- guillermocol (2)
- spommerening (2)
- adegoodyer (2)
- yermulnik (2)
- JonZeolla (2)
- ARaheem-Work (1)
- SayaliMane05 (1)
- verboEse (1)
- ansivul (1)
- ZNozomi (1)
- nbjohnson (1)
Pull Request Authors
- dependabot[bot] (73)
- nmoretenable (34)
- mandibles232 (26)
- bkizer-tenable (19)
- nbajaj-tenable (12)
- Rchanger (9)
- nasir-rabbani (8)
- nitumore (5)
- lisenet (4)
- hoexter (3)
- Adesoji1 (2)
- gukoff (2)
- sanjeeveejayabalan (2)
- zied-elouaer (2)
- jsnider-mtu (1)
Top Labels
Issue Labels
Pull Request Labels
Packages
- Total packages: 1
- Total downloads: unknown
- Total docker downloads: 9,046,021
- Total dependent packages: 0
- Total dependent repositories: 0
- Total versions: 57
proxy.golang.org: github.com/tenable/terrascan
- Homepage: https://github.com/tenable/terrascan
- Documentation: https://pkg.go.dev/github.com/tenable/terrascan#section-documentation
- License: Apache-2.0
-
Latest release: v1.19.9
published over 1 year ago
Rankings
Dependencies
- actions/checkout v2 composite
- actions/setup-go v1 composite
- codecov/codecov-action v1 composite
- docker/login-action v2 composite
- actions/checkout v2 composite
- actions/setup-go v2 composite
- docker/login-action v2 composite
- goreleaser/goreleaser-action v3 composite
- alpine 3.16 build
- golang alpine build
- tenable/terrascan ${TAG
- alpine 3.14.6 build
- runatlantis/atlantis v0.17.4 build
- runatlantis/atlantis v0.16.1 build
- runatlantis/atlantis v0.16.1 build
- runatlantis/atlantis v0.16.1 build
- runatlantis/atlantis v0.16.1 build
- runatlantis/atlantis v0.16.1 build
- runatlantis/atlantis v0.16.1 build
- runatlantis/atlantis v0.16.1 build
- runatlantis/atlantis v0.16.1 build
- runatlantis/atlantis v0.16.1 build
- cloud.google.com/go v0.105.0
- cloud.google.com/go/compute v1.14.0
- cloud.google.com/go/compute/metadata v0.2.3
- cloud.google.com/go/containeranalysis v0.6.0
- cloud.google.com/go/grafeas v0.2.0
- cloud.google.com/go/iam v0.8.0
- cloud.google.com/go/storage v1.27.0
- github.com/Azure/azure-sdk-for-go v56.3.0+incompatible
- github.com/Azure/go-autorest v14.2.0+incompatible
- github.com/Azure/go-autorest/autorest v0.11.24
- github.com/Azure/go-autorest/autorest/adal v0.9.18
- github.com/Azure/go-autorest/autorest/azure/auth v0.4.2
- github.com/Azure/go-autorest/autorest/azure/cli v0.4.2
- github.com/Azure/go-autorest/autorest/date v0.3.0
- github.com/Azure/go-autorest/autorest/validation v0.3.1
- github.com/Azure/go-autorest/logger v0.2.1
- github.com/Azure/go-autorest/tracing v0.6.0
- github.com/BurntSushi/toml v0.4.1
- github.com/GoogleCloudPlatform/docker-credential-gcr v2.0.5+incompatible
- github.com/Masterminds/goutils v1.1.1
- github.com/Masterminds/semver/v3 v3.1.1
- github.com/Masterminds/sprig/v3 v3.2.2
- github.com/OneOfOne/xxhash v1.2.8
- github.com/PuerkitoBio/purell v1.1.1
- github.com/PuerkitoBio/urlesc v0.0.0-20170810143723-de5bf2ad4578
- github.com/VerbalExpressions/GoVerbalExpressions v0.0.0-20200410162751-4d76a1099a6e
- github.com/agext/levenshtein v1.2.2
- github.com/agnivade/levenshtein v1.1.1
- github.com/apparentlymart/go-textseg/v13 v13.0.0
- github.com/apparentlymart/go-versions v1.0.1
- github.com/aws/aws-sdk-go v1.44.193
- github.com/aws/aws-sdk-go-v2 v1.7.1
- github.com/aws/aws-sdk-go-v2/config v1.5.0
- github.com/aws/aws-sdk-go-v2/credentials v1.3.1
- github.com/aws/aws-sdk-go-v2/feature/ec2/imds v1.3.0
- github.com/aws/aws-sdk-go-v2/feature/s3/manager v1.3.2
- github.com/aws/aws-sdk-go-v2/internal/ini v1.1.1
- github.com/aws/aws-sdk-go-v2/service/internal/accept-encoding v1.2.1
- github.com/aws/aws-sdk-go-v2/service/internal/presigned-url v1.2.1
- github.com/aws/aws-sdk-go-v2/service/internal/s3shared v1.5.1
- github.com/aws/aws-sdk-go-v2/service/s3 v1.11.1
- github.com/aws/aws-sdk-go-v2/service/sso v1.3.1
- github.com/aws/aws-sdk-go-v2/service/sts v1.6.0
- github.com/aws/smithy-go v1.6.0
- github.com/awslabs/goformation/v7 v7.0.5
- github.com/bgentry/go-netrc v0.0.0-20140422174119-9fd32a8b3d3d
- github.com/cespare/xxhash/v2 v2.2.0
- github.com/containerd/typeurl v1.0.2
- github.com/cyphar/filepath-securejoin v0.2.3
- github.com/davecgh/go-spew v1.1.1
- github.com/dgraph-io/badger/v3 v3.2103.4
- github.com/dimchansky/utfbom v1.1.1
- github.com/docker/cli v20.10.21+incompatible
- github.com/docker/distribution v2.8.1+incompatible
- github.com/docker/docker v20.10.24+incompatible
- github.com/docker/docker-credential-helpers v0.7.0
- github.com/docker/go-connections v0.4.0
- github.com/docker/go-units v0.5.0
- github.com/emirpasic/gods v1.12.0
- github.com/evanphx/json-patch v4.11.0+incompatible
- github.com/fatih/color v1.9.0
- github.com/felixge/httpsnoop v1.0.3
- github.com/fsnotify/fsnotify v1.6.0
- github.com/ghodss/yaml v1.0.0
- github.com/go-errors/errors v1.0.1
- github.com/go-logr/logr v1.2.3
- github.com/go-openapi/jsonpointer v0.19.5
- github.com/go-openapi/jsonreference v0.19.5
- github.com/go-openapi/swag v0.19.14
- github.com/go-task/slim-sprig v0.0.0-20210107165309-348f09dbbbc0
- github.com/gobwas/glob v0.2.3
- github.com/gogo/protobuf v1.3.2
- github.com/golang-jwt/jwt/v4 v4.2.0
- github.com/golang/groupcache v0.0.0-20210331224755-41bb18bfe9da
- github.com/golang/protobuf v1.5.2
- github.com/google/flatbuffers v22.11.23+incompatible
- github.com/google/go-cmp v0.5.9
- github.com/google/go-containerregistry v0.5.1
- github.com/google/gofuzz v1.2.0
- github.com/google/shlex v0.0.0-20191202100458-e7afc7fbc510
- github.com/google/uuid v1.3.0
- github.com/googleapis/enterprise-certificate-proxy v0.2.1
- github.com/googleapis/gax-go/v2 v2.7.0
- github.com/googleapis/gnostic v0.5.5
- github.com/gorilla/handlers v1.5.1
- github.com/gorilla/mux v1.8.0
- github.com/hashicorp/errwrap v1.1.0
- github.com/hashicorp/go-cleanhttp v0.5.2
- github.com/hashicorp/go-getter v1.6.2
- github.com/hashicorp/go-getter=>github.com/hashicorp/go-getter v1.6.1
- github.com/hashicorp/go-hclog v0.15.0
- github.com/hashicorp/go-multierror v1.1.1
- github.com/hashicorp/go-retryablehttp v0.6.6
- github.com/hashicorp/go-safetemp v1.0.0
- github.com/hashicorp/go-version v1.2.1
- github.com/hashicorp/hcl v1.0.0
- github.com/hashicorp/hcl/v2 v2.10.1
- github.com/hashicorp/terraform v0.15.3
- github.com/hashicorp/terraform-svchost v0.0.0-20200729002733-f050f53b9734
- github.com/huandu/xstrings v1.3.2
- github.com/iancoleman/strcase v0.1.3
- github.com/imdario/mergo v0.3.12
- github.com/inconshreveable/mousetrap v1.1.0
- github.com/itchyny/astgen-go v0.0.0-20210113000433-0da0671862a3
- github.com/itchyny/gojq v0.12.1
- github.com/itchyny/timefmt-go v0.1.1
- github.com/jbenet/go-context v0.0.0-20150711004518-d14ea06fba99
- github.com/jmespath/go-jmespath v0.4.0
- github.com/josharian/intern v1.0.0
- github.com/json-iterator/go v1.1.12
- github.com/kballard/go-shellquote v0.0.0-20180428030007-95032a82bc51
- github.com/kevinburke/ssh_config v0.0.0-20190725054713-01f96b0aa0cd
- github.com/klauspost/compress v1.15.13
- github.com/mailru/easyjson v0.7.6
- github.com/mattn/go-colorable v0.1.6
- github.com/mattn/go-isatty v0.0.12
- github.com/matttproud/golang_protobuf_extensions v1.0.4
- github.com/mitchellh/copystructure v1.1.1
- github.com/mitchellh/go-homedir v1.1.0
- github.com/mitchellh/go-testing-interface v1.0.0
- github.com/mitchellh/go-wordwrap v1.0.0
- github.com/mitchellh/panicwrap v1.0.0
- github.com/mitchellh/reflectwalk v1.0.1
- github.com/moby/buildkit v0.8.3
- github.com/modern-go/concurrent v0.0.0-20180306012644-bacd9c7ef1dd
- github.com/modern-go/reflect2 v1.0.2
- github.com/monochromegane/go-gitignore v0.0.0-20200626010858-205db1a8cc00
- github.com/nxadm/tail v1.4.8
- github.com/onsi/ginkgo v1.16.4
- github.com/onsi/gomega v1.22.1
- github.com/open-policy-agent/opa v0.46.1
- github.com/opencontainers/go-digest v1.0.0
- github.com/opencontainers/image-spec v1.1.0-rc2
- github.com/owenrumney/go-sarif/v2 v2.1.2
- github.com/pelletier/go-toml v1.9.3
- github.com/pkg/errors v0.9.1
- github.com/pmezard/go-difflib v1.0.0
- github.com/prometheus/client_golang v1.14.0
- github.com/prometheus/common v0.38.0
- github.com/rcrowley/go-metrics v0.0.0-20201227073835-cf1acfcdf475
- github.com/remyoudompheng/bigfft v0.0.0-20200410134404-eec4a21b6bb0
- github.com/sanathkr/go-yaml v0.0.0-20170819195128-ed9d249f429b
- github.com/sanathkr/yaml v0.0.0-20170819201035-0056894fa522
- github.com/sergi/go-diff v1.1.0
- github.com/shopspring/decimal v1.2.0
- github.com/sirupsen/logrus v1.9.0
- github.com/spf13/afero v1.6.0
- github.com/spf13/cast v1.3.1
- github.com/spf13/cobra v1.6.1
- github.com/spf13/pflag v1.0.5
- github.com/src-d/gcfg v1.4.0
- github.com/stretchr/testify v1.8.1
- github.com/tchap/go-patricia/v2 v2.3.1
- github.com/tencentcloud/tencentcloud-sdk-gov3.0.82+incompatible=>github.com/tencentcloud/tencentcloud-sdk-go v1.0.191
- github.com/ulikunitz/xz v0.5.8
- github.com/xanzy/ssh-agent v0.2.1
- github.com/xeipuuv/gojsonpointer v0.0.0-20190905194746-02993c407bfb
- github.com/xeipuuv/gojsonreference v0.0.0-20180127040603-bd5ef7bd5415
- github.com/xeipuuv/gojsonschema v1.2.0
- github.com/xlab/treeprint v0.0.0-20181112141820-a009c3971eca
- github.com/yashtewari/glob-intersection v0.1.0
- github.com/zclconf/go-cty v1.10.0
- go.opencensus.io v0.24.0
- go.starlark.net v0.0.0-20200306205701-8dd3e2ee1dd5
- go.uber.org/atomic v1.7.0
- go.uber.org/multierr v1.6.0
- go.uber.org/zap v1.17.0
- golang.org/x/crypto v0.0.0-20220525230936-793ad666bf5e
- golang.org/x/crypto=>golang.org/x/crypto v0.0.0-20211202192323-5770296d904e
- golang.org/x/mod v0.6.0-dev.0.20220419223038-86c51ed26bb4
- golang.org/x/net v0.4.0
- golang.org/x/net=>golang.org/x/net v0.4.0
- golang.org/x/oauth2 v0.2.0
- golang.org/x/sync v0.1.0
- golang.org/x/sys v0.3.0
- golang.org/x/term v0.3.0
- golang.org/x/text v0.5.0
- golang.org/x/time v0.3.0
- golang.org/x/tools v0.1.12
- golang.org/x/xerrors v0.0.0-20220907171357-04be3eba64a2
- google.golang.org/api v0.109.0
- google.golang.org/appengine v1.6.7
- google.golang.org/genproto v0.0.0-20221227171554-f9683d7f8bef
- google.golang.org/grpc v1.51.0
- google.golang.org/protobuf v1.28.1
- gopkg.in/inf.v0 v0.9.1
- gopkg.in/src-d/go-billy.v4 v4.3.2
- gopkg.in/src-d/go-git.v4 v4.13.1
- gopkg.in/tomb.v1 v1.0.0-20141024135613-dd632973f1e7
- gopkg.in/warnings.v0 v0.1.2
- gopkg.in/yaml.v2 v2.4.0
- gopkg.in/yaml.v3 v3.0.1
- helm.sh/helm/v3 v3.6.1
- k8s.io/api v0.22.5
- k8s.io/api=>k8s.io/api v0.19.0
- k8s.io/apiextensions-apiserver v0.21.0
- k8s.io/apimachinery v0.22.5
- k8s.io/apimachinery=>k8s.io/apimachinery v0.19.0
- k8s.io/client-go v10.0.0+incompatible
- k8s.io/client-go=>k8s.io/client-go v0.19.0
- k8s.io/klog/v2 v2.30.0
- k8s.io/kube-openapi v0.0.0-20211109043538-20434351676c
- k8s.io/utils v0.0.0-20210930125809-cb0fa318a74b
- lukechampine.com/uint128 v1.1.1
- modernc.org/cc/v3 v3.33.6
- modernc.org/ccgo/v3 v3.9.5
- modernc.org/libc v1.9.11
- modernc.org/mathutil v1.4.0
- modernc.org/memory v1.0.4
- modernc.org/opt v0.1.1
- modernc.org/sqlite v1.11.1
- modernc.org/strutil v1.1.1
- modernc.org/token v1.0.0
- sigs.k8s.io/kustomize/api v0.8.11
- sigs.k8s.io/kustomize/kyaml v0.11.0
- sigs.k8s.io/structured-merge-diff/v4 v4.1.2
- sigs.k8s.io/yaml v1.2.0
- 2092 dependencies
- mkdocs ==1.3.0
- mkdocs-diagrams ==1.0.0
- mkdocs-material ==8.2.14
- mkdocs-redirects ==1.0.3




