https://github.com/anchore/grype
A vulnerability scanner for container images and filesystems
Science Score: 26.0%
This score indicates how likely this project is to be science-related based on various indicators:
-
○CITATION.cff file
-
✓codemeta.json file
Found codemeta.json file -
✓.zenodo.json file
Found .zenodo.json file -
○DOI references
-
○Academic publication links
-
○Committers with academic emails
-
○Institutional organization owner
-
○JOSS paper metadata
-
○Scientific vocabulary similarity
Low similarity (9.6%) to scientific vocabulary
Keywords
Keywords from Contributors
Repository
A vulnerability scanner for container images and filesystems
Basic Info
Statistics
- Stars: 10,577
- Watchers: 80
- Forks: 682
- Open Issues: 332
- Releases: 0
Topics
Metadata Files
README.md

A vulnerability scanner for container images and filesystems. Easily [install the binary](#installation) to try it out. Works with [Syft](https://github.com/anchore/syft), the powerful SBOM (software bill of materials) tool for container images and filesystems.
### Join our community meetings!
- Calendar: https://calendar.google.com/calendar/u/0/r?cid=Y182OTM4dGt0MjRtajI0NnNzOThiaGtnM29qNEBncm91cC5jYWxlbmRhci5nb29nbGUuY29t
- Agenda: https://docs.google.com/document/d/1ZtSAa6fj2a6KRWviTn3WoJm09edvrNUp4Iz_dOjjyY8/edit?usp=sharing (join [this group](https://groups.google.com/g/anchore-oss-community) for write access)
- All are welcome!
For commercial support options with Syft or Grype, please [contact Anchore](https://get.anchore.com/contact/).
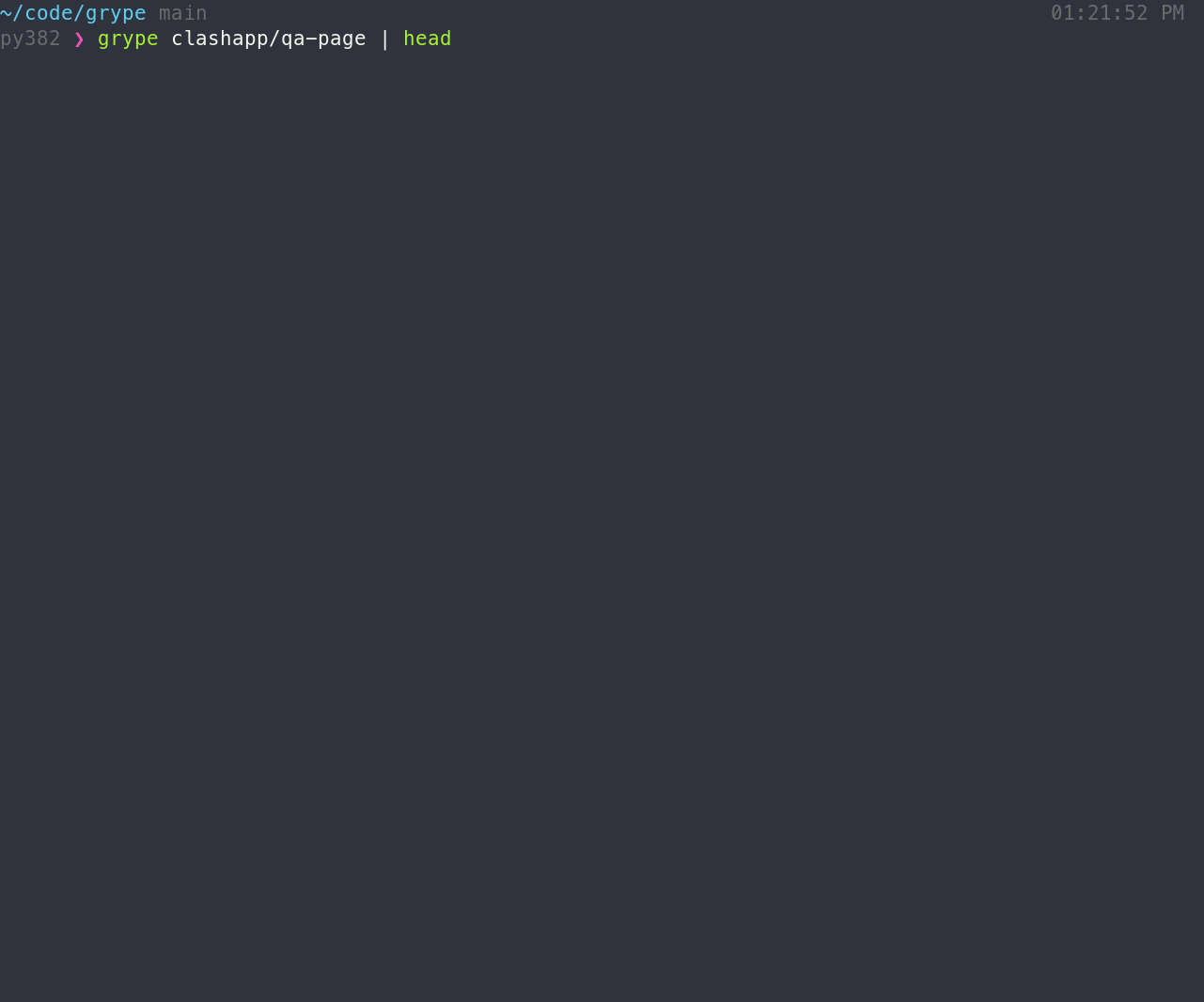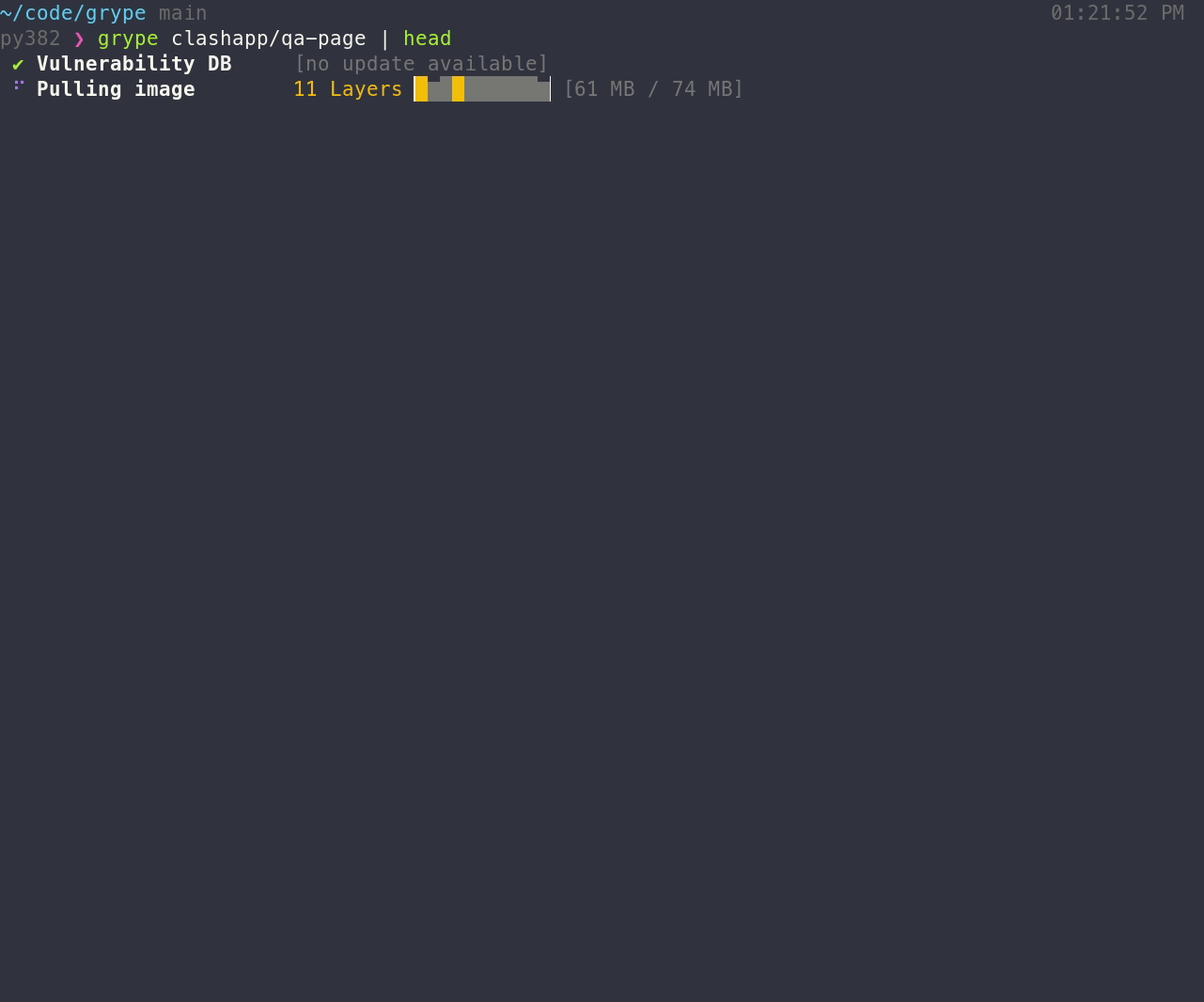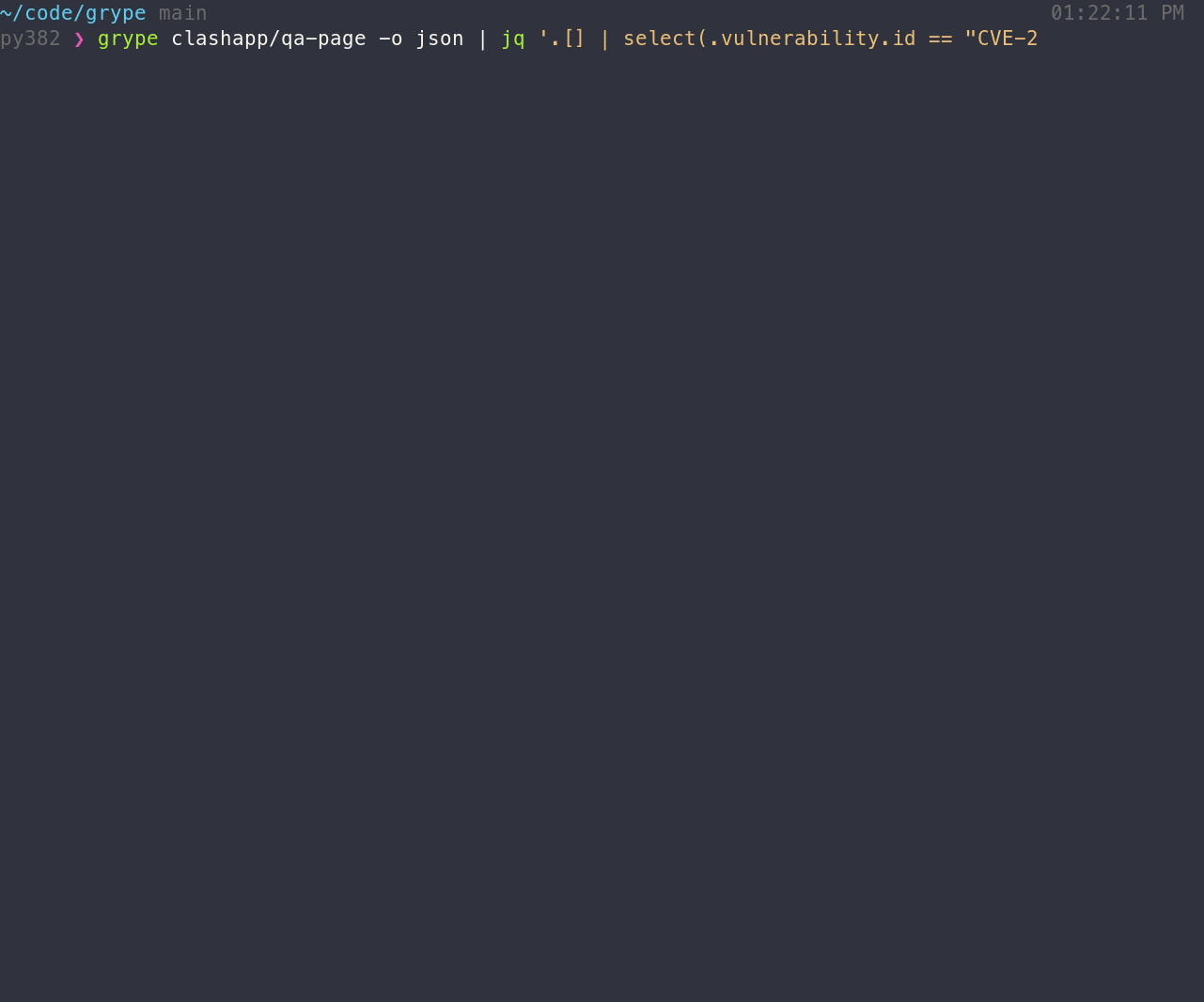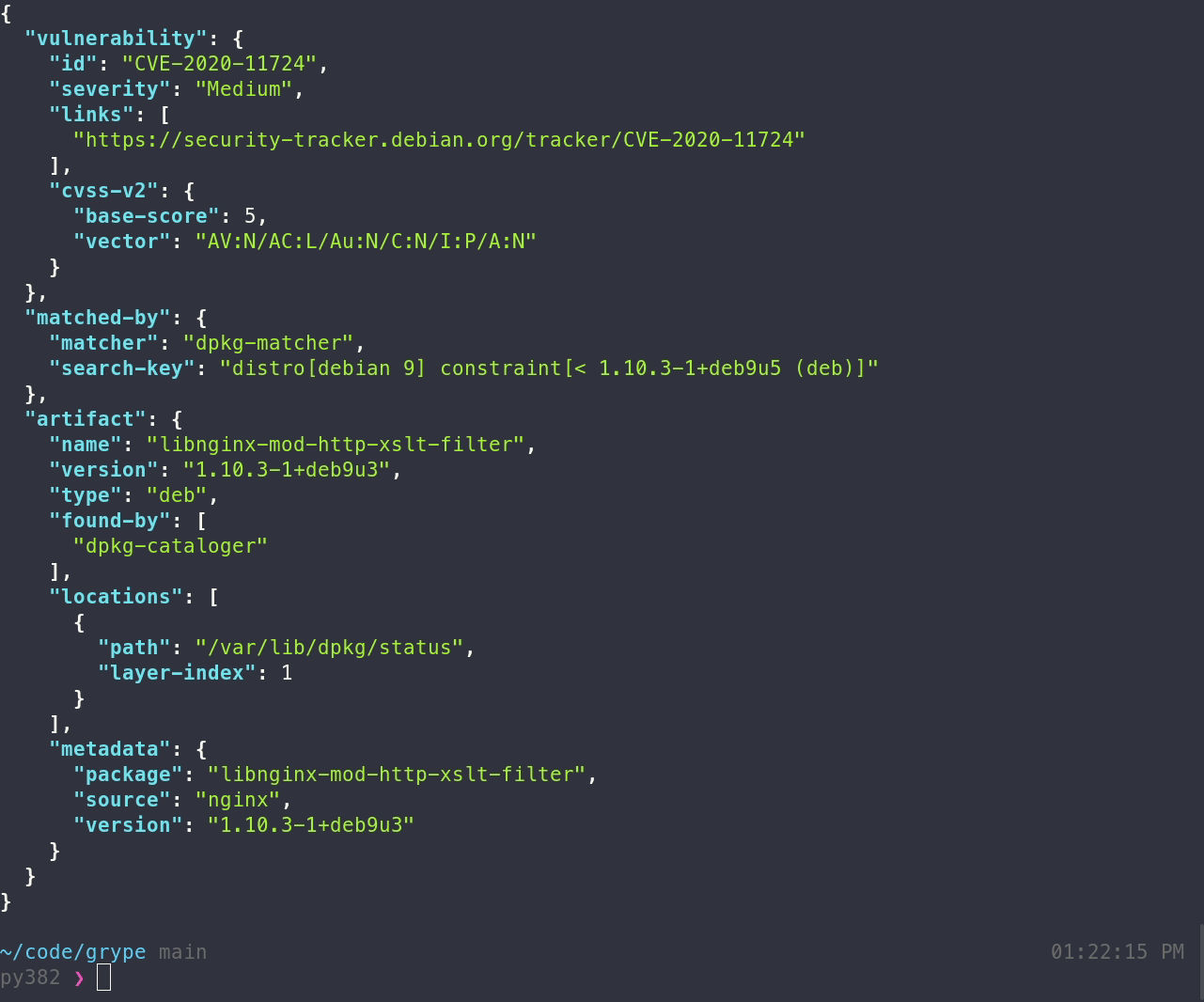
## Features
- Scan the contents of a container image or filesystem to find known vulnerabilities.
- Find vulnerabilities for major operating system packages:
- Alpine
- Amazon Linux
- Azure Linux (previously CBL-Mariner)
- BusyBox
- CentOS
- Debian
- Echo
- Distroless
- MinimOS
- Oracle Linux
- Red Hat (RHEL)
- Ubuntu
- Wolfi
- Find vulnerabilities for language-specific packages:
- Ruby (Gems)
- Java (JAR, WAR, EAR, JPI, HPI)
- JavaScript (NPM, Yarn)
- Python (Egg, Wheel, Poetry, requirements.txt/setup.py files)
- Dotnet (deps.json)
- Golang (go.mod)
- PHP (Composer)
- Rust (Cargo)
- Supports Docker, OCI and [Singularity](https://github.com/sylabs/singularity) image formats.
- [OpenVEX](https://github.com/openvex) support for filtering and augmenting scanning results.
If you encounter an issue, please [let us know using the issue tracker](https://github.com/anchore/grype/issues).
## Installation
### Recommended
```bash
curl -sSfL https://get.anchore.io/grype | sudo sh -s -- -b /usr/local/bin
```
Install script options:
- `-b`: Specify a custom installation directory (defaults to `./bin`)
- `-d`: More verbose logging levels (`-d` for debug, `-dd` for trace)
- `-v`: Verify the signature of the downloaded artifact before installation (requires [`cosign`](https://github.com/sigstore/cosign) to be installed)
### Chocolatey
The chocolatey distribution of grype is community-maintained and not distributed by the anchore team.
```bash
choco install grype -y
```
### Homebrew
```bash
brew tap anchore/grype
brew install grype
```
### MacPorts
On macOS, Grype can additionally be installed from the [community-maintained port](https://ports.macports.org/port/grype/) via MacPorts:
```bash
sudo port install grype
```
**Note**: Currently, Grype is built only for macOS and Linux.
### From source
See [DEVELOPING.md](DEVELOPING.md#native-development) for instructions to build and run from source.
### GitHub Actions
If you're using GitHub Actions, you can use our [Grype-based action](https://github.com/marketplace/actions/anchore-container-scan) to run vulnerability scans on your code or container images during your CI workflows.
## Verifying the artifacts
Checksums are applied to all artifacts, and the resulting checksum file is signed using cosign.
You need the following tool to verify signature:
- [Cosign](https://docs.sigstore.dev/cosign/system_config/installation/)
Verification steps are as follow:
1. Download the files you want, and the checksums.txt, checksums.txt.pem and checksums.txt.sig files from the [releases](https://github.com/anchore/grype/releases) page:
2. Verify the signature:
```shell
cosign verify-blob Grype Logo by Anchore is licensed under CC BY 4.0
Owner
- Name: Anchore, Inc.
- Login: anchore
- Kind: organization
- Email: info@anchore.com
- Website: https://anchore.com/
- Repositories: 43
- Profile: https://github.com/anchore
Committers
Last synced: 9 months ago
Top Committers
| Name | Commits | |
|---|---|---|
| dependabot[bot] | 4****] | 427 |
| Alex Goodman | w****n | 381 |
| anchore-actions-token-generator[bot] | 1****] | 204 |
| Christopher Angelo Phillips | 3****s | 101 |
| Dan Luhring | l****g | 87 |
| Alfredo Deza | a****a@a****m | 83 |
| Keith Zantow | k****w@g****m | 83 |
| Weston Steimel | w****l@a****m | 63 |
| William Murphy | w****y@a****m | 48 |
| cpendery | 3****y | 16 |
| Jonas Xavier | j****x@g****m | 11 |
| Alan Pope | a****e@a****m | 6 |
| Vijay Pillai | v****i@a****m | 6 |
| Samuel Dacanay | s****y@a****m | 5 |
| guangwu | g****g@g****m | 5 |
| James Neate | J****e@g****m | 4 |
| Zach Hill | z****h@a****m | 4 |
| Joyce | j****m@g****m | 3 |
| Adam Hughes | 9****m | 3 |
| Bar Nuri | b****i@h****m | 3 |
| Conor Nosal | c****l@v****m | 3 |
| GGMU | 4****n | 3 |
| Seiya | 2****b | 3 |
| briankoe741 | 1****1 | 3 |
| Arvind Somya | a****a@a****m | 2 |
| Abhijeet Kasurde | a****e@r****m | 2 |
| Michael de Senna | d****a | 2 |
| Puerco | p****o | 2 |
| Ross Turk | r****s@r****m | 2 |
| Shane Dell | 3****l | 2 |
| and 79 more... | ||
Committer Domains (Top 20 + Academic)
Issues and Pull Requests
Last synced: 6 months ago
All Time
- Total issues: 631
- Total pull requests: 1,807
- Average time to close issues: 7 months
- Average time to close pull requests: 6 days
- Total issue authors: 336
- Total pull request authors: 82
- Average comments per issue: 2.45
- Average comments per pull request: 0.31
- Merged pull requests: 1,425
- Bot issues: 9
- Bot pull requests: 1,071
Past Year
- Issues: 223
- Pull requests: 989
- Average time to close issues: 10 days
- Average time to close pull requests: 3 days
- Issue authors: 129
- Pull request authors: 47
- Average comments per issue: 1.02
- Average comments per pull request: 0.24
- Merged pull requests: 751
- Bot issues: 6
- Bot pull requests: 558
Top Authors
Issue Authors
- sekveaja (67)
- wagoodman (46)
- willmurphyscode (21)
- luhring (18)
- tomersein (14)
- kzantow (13)
- chovanecadam (8)
- metametadata (8)
- TimBrown1611 (8)
- tomerse-sg (7)
- dbrugman (6)
- karthickm512 (5)
- Dentrax (5)
- anchore-actions-token-generator[bot] (5)
- mirekphd (4)
Pull Request Authors
- dependabot[bot] (767)
- anchore-actions-token-generator[bot] (304)
- wagoodman (241)
- willmurphyscode (94)
- kzantow (92)
- spiffcs (49)
- westonsteimel (48)
- luhring (18)
- popey (12)
- tomersein (9)
- testwill (9)
- zhill (8)
- seiyab (5)
- OnceUponALoop (5)
- patrickjburke245 (5)
Top Labels
Issue Labels
Pull Request Labels
Dependencies
- actions/cache 9b0c1fce7a93df8e3bb8926b0d6e9d89e92f20a7 composite
- actions/checkout 93ea575cb5d8a053eaa0ac8fa3b40d7e05a33cc8 composite
- actions/setup-go c4a742cab115ed795e34d4513e2cf7d472deb55f composite
- github/codeql-action/analyze c3b6fce4ee2ca25bc1066aa3bf73962fda0e8898 composite
- github/codeql-action/init c3b6fce4ee2ca25bc1066aa3bf73962fda0e8898 composite
- 8398a7/action-slack a189acbf0b7ea434558662ae25a0de71df69a435 composite
- actions/cache 9b0c1fce7a93df8e3bb8926b0d6e9d89e92f20a7 composite
- actions/checkout e2f20e631ae6d7dd3b768f56a5d2af784dd54791 composite
- actions/setup-go c4a742cab115ed795e34d4513e2cf7d472deb55f composite
- actions/upload-artifact 83fd05a356d7e2593de66fc9913b3002723633cb composite
- anchore/sbom-action 06e109483e6aa305a2b2395eabae554e51530e1d composite
- docker/login-action f4ef78c080cd8ba55a85445d5b36e214a81df20a composite
- fountainhead/action-wait-for-check 297be350cf8393728ea4d4b39435c7d7ae167c93 composite
- actions/checkout a12a3943b4bdde767164f792f33f40b04645d846 composite
- github/codeql-action/upload-sarif 5f532563584d71fdef14ee64d17bafb34f751ce5 composite
- ossf/scorecard-action 99c53751e09b9529366343771cc321ec74e9bd3d composite
- actions/checkout e2f20e631ae6d7dd3b768f56a5d2af784dd54791 composite
- actions/setup-go c4a742cab115ed795e34d4513e2cf7d472deb55f composite
- peter-evans/create-pull-request b4d51739f96fca8047ad065eccef63442d8e99f7 composite
- tibdex/github-app-token 021a2405c7f990db57f5eae5397423dcc554159c composite
- actions/checkout e2f20e631ae6d7dd3b768f56a5d2af784dd54791 composite
- actions/setup-go c4a742cab115ed795e34d4513e2cf7d472deb55f composite
- peter-evans/create-pull-request b4d51739f96fca8047ad065eccef63442d8e99f7 composite
- tibdex/github-app-token 021a2405c7f990db57f5eae5397423dcc554159c composite
- gcr.io/distroless/static-debian11@sha256 5759d194607e472ff80fff5833442d3991dd89b219c96552837a2c8f74058617 build
- scratch latest build
- actions/cache 9b0c1fce7a93df8e3bb8926b0d6e9d89e92f20a7 composite
- actions/checkout e2f20e631ae6d7dd3b768f56a5d2af784dd54791 composite
- actions/download-artifact 9782bd6a9848b53b110e712e20e42d89988822b7 composite
- actions/setup-go c4a742cab115ed795e34d4513e2cf7d472deb55f composite
- actions/setup-python 13ae5bb136fac2878aff31522b9efb785519f984 composite
- actions/upload-artifact 83fd05a356d7e2593de66fc9913b3002723633cb composite
- docker/setup-qemu-action e81a89b1732b9c48d79cd809d8d81d79c4647a18 composite
- scratch latest build
- scratch latest build
- scratch latest build
- scratch latest build
- openjdk 15-slim-buster build
- node 16-stretch build
- scratch latest build
- docker.io/archlinux 20191105@sha256 build
- scratch latest build
- docker.io/golang 1.16@sha256 build
- scratch latest build
- scratch latest build
- scratch latest build
- bitbucket.org/creachadair/shell v0.0.7
- cloud.google.com/go v0.104.0
- cloud.google.com/go/compute v1.10.0
- cloud.google.com/go/iam v0.5.0
- cloud.google.com/go/storage v1.23.0
- github.com/Azure/go-autorest v14.2.0+incompatible
- github.com/Azure/go-autorest/autorest v0.11.28
- github.com/Azure/go-autorest/autorest/adal v0.9.21
- github.com/Azure/go-autorest/autorest/date v0.3.0
- github.com/Azure/go-autorest/logger v0.2.1
- github.com/Azure/go-autorest/tracing v0.6.0
- github.com/CycloneDX/cyclonedx-go v0.7.1-0.20221222100750-41a1ac565cce
- github.com/DataDog/zstd v1.4.5
- github.com/Masterminds/goutils v1.1.1
- github.com/Masterminds/semver/v3 v3.1.1
- github.com/Masterminds/sprig/v3 v3.2.2
- github.com/Microsoft/go-winio v0.5.2
- github.com/ThalesIgnite/crypto11 v1.2.5
- github.com/acarl005/stripansi v0.0.0-20180116102854-5a71ef0e047d
- github.com/acobaugh/osrelease v0.1.0
- github.com/adrg/xdg v0.3.3
- github.com/anchore/go-logger v0.0.0-20220728155337-03b66a5207d8
- github.com/anchore/go-macholibre v0.0.0-20220308212642-53e6d0aaf6fb
- github.com/anchore/go-testutils v0.0.0-20200925183923-d5f45b0d3c04
- github.com/anchore/go-version v1.2.2-0.20210903204242-51efa5b487c4
- github.com/anchore/packageurl-go v0.1.1-0.20220428202044-a072fa3cb6d7
- github.com/anchore/sqlite v1.4.6-0.20220607210448-bcc6ee5c4963
- github.com/anchore/stereoscope v0.0.0-20221208011002-c5ff155d72f1
- github.com/anchore/syft v0.65.0
- github.com/andybalholm/brotli v1.0.4
- github.com/asaskevich/govalidator v0.0.0-20210307081110-f21760c49a8d
- github.com/aws/aws-sdk-go v1.44.114
- github.com/benbjohnson/clock v1.1.0
- github.com/beorn7/perks v1.0.1
- github.com/bgentry/go-netrc v0.0.0-20140422174119-9fd32a8b3d3d
- github.com/bgentry/speakeasy v0.1.0
- github.com/blang/semver v3.5.1+incompatible
- github.com/bmatcuk/doublestar/v2 v2.0.4
- github.com/bmatcuk/doublestar/v4 v4.0.2
- github.com/cenkalti/backoff/v4 v4.1.3
- github.com/census-instrumentation/opencensus-proto v0.3.0
- github.com/cespare/xxhash/v2 v2.1.2
- github.com/cncf/udpa/go v0.0.0-20210930031921-04548b0d99d4
- github.com/cncf/xds/go v0.0.0-20211130200136-a8f946100490
- github.com/containerd/containerd v1.6.12
- github.com/containerd/stargz-snapshotter/estargz v0.12.0
- github.com/coreos/go-semver v0.3.0
- github.com/coreos/go-systemd/v22 v22.3.2
- github.com/cpuguy83/go-md2man/v2 v2.0.2
- github.com/cyberphone/json-canonicalization v0.0.0-20210823021906-dc406ceaf94b
- github.com/davecgh/go-spew v1.1.1
- github.com/docker/cli v20.10.17+incompatible
- github.com/docker/distribution v2.8.1+incompatible
- github.com/docker/docker v20.10.17+incompatible
- github.com/docker/docker-credential-helpers v0.6.4
- github.com/docker/go-connections v0.4.0
- github.com/docker/go-units v0.4.0
- github.com/dsnet/compress v0.0.2-0.20210315054119-f66993602bf5
- github.com/dustin/go-humanize v1.0.0
- github.com/envoyproxy/go-control-plane v0.10.2-0.20220325020618-49ff273808a1
- github.com/envoyproxy/protoc-gen-validate v0.6.2
- github.com/facebookincubator/nvdtools v0.1.4
- github.com/fsnotify/fsnotify v1.5.4
- github.com/fullstorydev/grpcurl v1.8.7
- github.com/gabriel-vasile/mimetype v1.4.0
- github.com/go-chi/chi v4.1.2+incompatible
- github.com/go-logr/logr v1.2.3
- github.com/go-logr/stdr v1.2.2
- github.com/go-openapi/analysis v0.21.4
- github.com/go-openapi/errors v0.20.3
- github.com/go-openapi/jsonpointer v0.19.5
- github.com/go-openapi/jsonreference v0.20.0
- github.com/go-openapi/loads v0.21.2
- github.com/go-openapi/runtime v0.24.2
- github.com/go-openapi/spec v0.20.7
- github.com/go-openapi/strfmt v0.21.3
- github.com/go-openapi/swag v0.22.3
- github.com/go-openapi/validate v0.22.0
- github.com/go-playground/locales v0.14.0
- github.com/go-playground/universal-translator v0.18.0
- github.com/go-playground/validator/v10 v10.11.0
- github.com/go-restruct/restruct v1.2.0-alpha
- github.com/go-test/deep v1.0.8
- github.com/gogo/protobuf v1.3.2
- github.com/golang-jwt/jwt v3.2.2+incompatible
- github.com/golang-jwt/jwt/v4 v4.4.2
- github.com/golang/glog v1.0.0
- github.com/golang/groupcache v0.0.0-20210331224755-41bb18bfe9da
- github.com/golang/mock v1.6.0
- github.com/golang/protobuf v1.5.2
- github.com/golang/snappy v0.0.4
- github.com/google/btree v1.1.2
- github.com/google/certificate-transparency-go v1.1.3
- github.com/google/go-cmp v0.5.9
- github.com/google/go-containerregistry v0.11.0
- github.com/google/go-github/v45 v45.2.0
- github.com/google/go-querystring v1.1.0
- github.com/google/gofuzz v1.2.0
- github.com/google/trillian v1.5.0
- github.com/google/uuid v1.3.0
- github.com/googleapis/enterprise-certificate-proxy v0.2.0
- github.com/googleapis/gax-go/v2 v2.5.1
- github.com/googleapis/gnostic v0.5.5
- github.com/googleapis/go-type-adapters v1.0.0
- github.com/gookit/color v1.4.2
- github.com/gorilla/websocket v1.4.2
- github.com/grpc-ecosystem/go-grpc-middleware v1.3.0
- github.com/grpc-ecosystem/go-grpc-prometheus v1.2.0
- github.com/grpc-ecosystem/grpc-gateway v1.16.0
- github.com/grpc-ecosystem/grpc-gateway/v2 v2.11.3
- github.com/hako/durafmt v0.0.0-20210608085754-5c1018a4e16b
- github.com/hashicorp/errwrap v1.1.0
- github.com/hashicorp/go-cleanhttp v0.5.2
- github.com/hashicorp/go-getter v1.6.1
- github.com/hashicorp/go-multierror v1.1.1
- github.com/hashicorp/go-retryablehttp v0.7.1
- github.com/hashicorp/go-safetemp v1.0.0
- github.com/hashicorp/go-version v1.6.0
- github.com/hashicorp/hcl v1.0.0
- github.com/huandu/xstrings v1.3.2
- github.com/imdario/mergo v0.3.12
- github.com/in-toto/in-toto-golang v0.4.1-0.20221018183522-731d0640b65f
- github.com/inconshreveable/mousetrap v1.0.1
- github.com/jedisct1/go-minisign v0.0.0-20211028175153-1c139d1cc84b
- github.com/jhump/protoreflect v1.13.0
- github.com/jinzhu/copier v0.3.2
- github.com/jinzhu/inflection v1.0.0
- github.com/jinzhu/now v1.1.4
- github.com/jmespath/go-jmespath v0.4.0
- github.com/jonboulle/clockwork v0.3.0
- github.com/josharian/intern v1.0.0
- github.com/json-iterator/go v1.1.12
- github.com/kballard/go-shellquote v0.0.0-20180428030007-95032a82bc51
- github.com/klauspost/compress v1.15.9
- github.com/klauspost/pgzip v1.2.5
- github.com/knqyf263/go-apk-version v0.0.0-20200609155635-041fdbb8563f
- github.com/knqyf263/go-deb-version v0.0.0-20190517075300-09fca494f03d
- github.com/knqyf263/go-rpmdb v0.0.0-20221030135625-4082a22221ce
- github.com/leodido/go-urn v1.2.1
- github.com/letsencrypt/boulder v0.0.0-20220929215747-76583552c2be
- github.com/logrusorgru/aurora v0.0.0-20200102142835-e9ef32dff381
- github.com/magiconair/properties v1.8.6
- github.com/mailru/easyjson v0.7.7
- github.com/mattn/go-colorable v0.1.13
- github.com/mattn/go-isatty v0.0.16
- github.com/mattn/go-runewidth v0.0.13
- github.com/matttproud/golang_protobuf_extensions v1.0.4
- github.com/mgutz/ansi v0.0.0-20200706080929-d51e80ef957d
- github.com/mholt/archiver/v3 v3.5.1
- github.com/microsoft/go-rustaudit v0.0.0-20220730194248-4b17361d90a5
- github.com/miekg/pkcs11 v1.1.1
- github.com/mitchellh/copystructure v1.2.0
- github.com/mitchellh/go-homedir v1.1.0
- github.com/mitchellh/go-testing-interface v1.14.1
- github.com/mitchellh/hashstructure/v2 v2.0.2
- github.com/mitchellh/mapstructure v1.5.0
- github.com/mitchellh/reflectwalk v1.0.2
- github.com/moby/term v0.0.0-20210619224110-3f7ff695adc6
- github.com/modern-go/concurrent v0.0.0-20180306012644-bacd9c7ef1dd
- github.com/modern-go/reflect2 v1.0.2
- github.com/nwaples/rardecode v1.1.0
- github.com/oklog/ulid v1.3.1
- github.com/olekukonko/tablewriter v0.0.5
- github.com/opencontainers/go-digest v1.0.0
- github.com/opencontainers/image-spec v1.0.3-0.20220114050600-8b9d41f48198
- github.com/opentracing/opentracing-go v1.2.0
- github.com/owenrumney/go-sarif v1.1.1
- github.com/pelletier/go-toml v1.9.5
- github.com/pelletier/go-toml/v2 v2.0.5
- github.com/pierrec/lz4/v4 v4.1.15
- github.com/pkg/errors v0.9.1
- github.com/pkg/profile v1.6.0
- github.com/pmezard/go-difflib v1.0.0
- github.com/prometheus/client_golang v1.13.0
- github.com/prometheus/client_model v0.2.0
- github.com/prometheus/common v0.37.0
- github.com/prometheus/procfs v0.8.0
- github.com/remyoudompheng/bigfft v0.0.0-20200410134404-eec4a21b6bb0
- github.com/rivo/uniseg v0.2.0
- github.com/russross/blackfriday/v2 v2.1.0
- github.com/sassoftware/go-rpmutils v0.2.0
- github.com/sassoftware/relic v0.0.0-20210427151427-dfb082b79b74
- github.com/scylladb/go-set v1.0.3-0.20200225121959-cc7b2070d91e
- github.com/secure-systems-lab/go-securesystemslib v0.4.0
- github.com/sergi/go-diff v1.2.0
- github.com/shibumi/go-pathspec v1.3.0
- github.com/shopspring/decimal v1.2.0
- github.com/sigstore/cosign v1.13.1
- github.com/sigstore/rekor v0.12.1-0.20220915152154-4bb6f441c1b2
- github.com/sigstore/sigstore v1.4.4
- github.com/sirupsen/logrus v1.9.0
- github.com/soheilhy/cmux v0.1.5
- github.com/spdx/tools-golang v0.3.1-0.20221108182156-8a01147e6342
- github.com/spf13/afero v1.8.2
- github.com/spf13/cast v1.5.0
- github.com/spf13/cobra v1.6.0
- github.com/spf13/jwalterweatherman v1.1.0
- github.com/spf13/pflag v1.0.5
- github.com/spf13/viper v1.13.0
- github.com/stretchr/objx v0.5.0
- github.com/stretchr/testify v1.8.1
- github.com/subosito/gotenv v1.4.1
- github.com/sylabs/sif/v2 v2.8.1
- github.com/sylabs/squashfs v0.6.1
- github.com/syndtr/goleveldb v1.0.1-0.20220721030215-126854af5e6d
- github.com/tent/canonical-json-go v0.0.0-20130607151641-96e4ba3a7613
- github.com/thales-e-security/pool v0.0.2
- github.com/therootcompany/xz v1.0.1
- github.com/theupdateframework/go-tuf v0.5.2-0.20220930112810-3890c1e7ace4
- github.com/titanous/rocacheck v0.0.0-20171023193734-afe73141d399
- github.com/tmc/grpc-websocket-proxy v0.0.0-20201229170055-e5319fda7802
- github.com/transparency-dev/merkle v0.0.1
- github.com/ulikunitz/xz v0.5.10
- github.com/urfave/cli v1.22.7
- github.com/vbatts/go-mtree v0.5.0
- github.com/vbatts/tar-split v0.11.2
- github.com/vifraa/gopom v0.1.0
- github.com/wagoodman/go-partybus v0.0.0-20210627031916-db1f5573bbc5
- github.com/wagoodman/go-progress v0.0.0-20200807221327-51d465df1451
- github.com/wagoodman/jotframe v0.0.0-20211129225309-56b0d0a4aebb
- github.com/x-cray/logrus-prefixed-formatter v0.5.2
- github.com/xanzy/go-gitlab v0.73.1
- github.com/xi2/xz v0.0.0-20171230120015-48954b6210f8
- github.com/xiang90/probing v0.0.0-20190116061207-43a291ad63a2
- github.com/xo/terminfo v0.0.0-20210125001918-ca9a967f8778
- github.com/zclconf/go-cty v1.10.0
- go.etcd.io/bbolt v1.3.6
- go.etcd.io/etcd/api/v3 v3.6.0-alpha.0
- go.etcd.io/etcd/client/pkg/v3 v3.6.0-alpha.0
- go.etcd.io/etcd/client/v2 v2.306.0-alpha.0
- go.etcd.io/etcd/client/v3 v3.6.0-alpha.0
- go.etcd.io/etcd/etcdctl/v3 v3.6.0-alpha.0
- go.etcd.io/etcd/etcdutl/v3 v3.6.0-alpha.0
- go.etcd.io/etcd/pkg/v3 v3.6.0-alpha.0
- go.etcd.io/etcd/raft/v3 v3.6.0-alpha.0
- go.etcd.io/etcd/server/v3 v3.6.0-alpha.0
- go.etcd.io/etcd/tests/v3 v3.6.0-alpha.0
- go.etcd.io/etcd/v3 v3.6.0-alpha.0
- go.mongodb.org/mongo-driver v1.10.0
- go.opencensus.io v0.23.0
- go.opentelemetry.io/contrib/instrumentation/google.golang.org/grpc/otelgrpc v0.28.0
- go.opentelemetry.io/otel v1.7.0
- go.opentelemetry.io/otel/exporters/otlp/internal/retry v1.7.0
- go.opentelemetry.io/otel/exporters/otlp/otlptrace v1.7.0
- go.opentelemetry.io/otel/exporters/otlp/otlptrace/otlptracegrpc v1.7.0
- go.opentelemetry.io/otel/sdk v1.7.0
- go.opentelemetry.io/otel/trace v1.7.0
- go.opentelemetry.io/proto/otlp v0.16.0
- go.uber.org/atomic v1.10.0
- go.uber.org/multierr v1.8.0
- go.uber.org/zap v1.23.0
- golang.org/x/crypto v0.0.0-20220926161630-eccd6366d1be
- golang.org/x/exp v0.0.0-20220823124025-807a23277127
- golang.org/x/mod v0.6.0-dev.0.20220419223038-86c51ed26bb4
- golang.org/x/net v0.0.0-20221012135044-0b7e1fb9d458
- golang.org/x/oauth2 v0.0.0-20221006150949-b44042a4b9c1
- golang.org/x/sync v0.1.0
- golang.org/x/sys v0.0.0-20220928140112-f11e5e49a4ec
- golang.org/x/term v0.0.0-20220919170432-7a66f970e087
- golang.org/x/text v0.3.8-0.20211004125949-5bd84dd9b33b
- golang.org/x/time v0.0.0-20220922220347-f3bd1da661af
- golang.org/x/tools v0.1.12
- golang.org/x/xerrors v0.0.0-20220907171357-04be3eba64a2
- google.golang.org/api v0.99.0
- google.golang.org/appengine v1.6.7
- google.golang.org/genproto v0.0.0-20221010155953-15ba04fc1c0e
- google.golang.org/grpc v1.50.1
- google.golang.org/protobuf v1.28.1
- gopkg.in/cheggaaa/pb.v1 v1.0.28
- gopkg.in/inf.v0 v0.9.1
- gopkg.in/ini.v1 v1.67.0
- gopkg.in/natefinch/lumberjack.v2 v2.0.0
- gopkg.in/square/go-jose.v2 v2.6.0
- gopkg.in/yaml.v2 v2.4.0
- gopkg.in/yaml.v3 v3.0.1
- gorm.io/gorm v1.23.5
- k8s.io/api v0.23.5
- k8s.io/apimachinery v0.23.5
- k8s.io/client-go v0.23.5
- k8s.io/klog/v2 v2.60.1-0.20220317184644-43cc75f9ae89
- k8s.io/kube-openapi v0.0.0-20220124234850-424119656bbf
- k8s.io/utils v0.0.0-20220210201930-3a6ce19ff2f9
- lukechampine.com/uint128 v1.1.1
- modernc.org/cc/v3 v3.36.0
- modernc.org/ccgo/v3 v3.16.6
- modernc.org/libc v1.16.8
- modernc.org/mathutil v1.4.1
- modernc.org/memory v1.1.1
- modernc.org/opt v0.1.1
- modernc.org/sqlite v1.17.3
- modernc.org/strutil v1.1.1
- modernc.org/token v1.0.0
- sigs.k8s.io/json v0.0.0-20211208200746-9f7c6b3444d2
- sigs.k8s.io/structured-merge-diff/v4 v4.2.1
- sigs.k8s.io/yaml v1.3.0
- 2758 dependencies
- github.com/google/uuid v1.3.0
- github.com/google/uuid v1.3.0
- left-pad 1.3.0
- lodash 4.17.21
- deep-equal ^1.0.1 development
- get-stream ^4.1.0 development
- licensee ^7.0.3 development
- marked ^0.6.3 development
- marked-man ^0.6.0 development
- npm-registry-couchapp ^2.7.4 development
- npm-registry-mock ^1.3.1 development
- require-inject ^1.4.4 development
- sprintf-js ^1.1.2 development
- standard ^11.0.1 development
- tacks ^1.3.0 development
- tap ^12.7.0 development
- tar-stream ^2.1.0 development
- JSONStream ^1.3.5
- abbrev ~1.1.1
- ansicolors ~0.3.2
- write-file-atomic ^2.4.3
- tabulate ==0.8.10 test
- rails 4.1.1




